49 Discuss AAA and various protocols that provide AAA features AAA (Authentication, Authorization and Accounting)
AAA provides high level of security to the network devices. AAA architecture provides secure access to the network and network devices. The three functional components of AAA are:
1) Authentication
2) Authorization
3) Accounting and auditing
Authentication: It requires the network administrator and users to be checked before they enter into the network. It requires the users to enter into the network with the use of username and password.
Authorization: After the users whether they are normal user or administrators enter into the network with the proper authentication need to be only given access to the resources that they are allowed to access. Other authorization tasks are:
1) Assigning parameters such as IP address and access control lists (ACL) to the connected users.
2) Controlling the level of commands users can run on the network devices.
Accounting: It keeps a record of what activities the users and administrator performed while they accessed the devices and for how long they accessed the devices in the network. For example accounting tells us that ABC user logged via telnet for 10 minutes. AAA uses two protocols to implement security:
1) RADIUS
2) TACACS+
Remote Authentication Dial-In User Service (RADIUS)
RADIUS was developed by the Internet Engineering Task Force (IETF). It safeguards the network from unauthorized access. It is an open standard solution to implement security as RADIUS being an open standard it is used by most security servers. RADIUS uses client server architecture where the client is the router and the web server is the operating system running RADIUS software.
There are four types of RADIUS message:
1) Access-Request
2) Access-Challenge
3) Access-Accept
4) Access-Reject Working of RADIUS
Workstation File
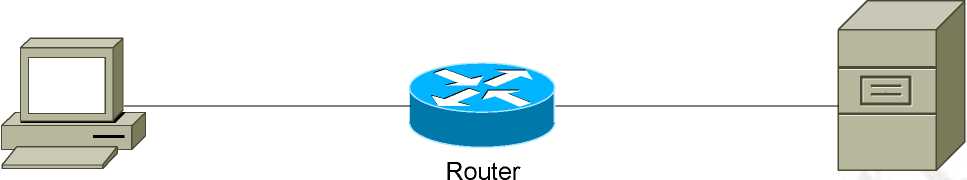
Figure 82: Radius Working
In this figure the Workstation is authenticated into the network with the use of RADIUS.
The working of RADIUS is defined in below process:
Server
1) The Network Access System prompts the client for the username
2) The client provides a username to the network access system
3) NAS prompts for a password
4) The client provides the password to the server
5) The username and password is sent to the RADIUS server.
6) If the supplied information is correct the RADIUS server responds with an Access-Accept datagram. If the information provided by the user is incorrect an Access-Reject message is returned and NAS then terminates the connection
Router(config)# aaa new-model
Router(config)# radius-server host 10.0.0.1 single connection Router(config)# radius-server key shared2
Terminal Access Controller Access Control System (TACACS+)
It is used to provide security to the network devices access. It is more flexible than RADIUS. In some ways TACACS+ is similar to RADIUS. It is not an open standard protocol it is developed by Cisco Systems to interact with Cisco AAA servers. In case of implementing TACACS+ we can implement all AAA features.
Workstation File
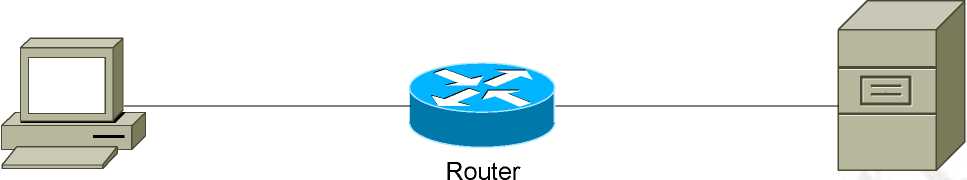
Figure 83: TACAS+
Server
In the above diagram the workstation is authenticated with the TACACS+. The various steps followed are as follows:
1) A user requests access.
2) NAC requests a username prompt from the TACACS+ server.
3) The TACACS+ server provides a username prompt.
4) NAC prompts the user.
5) The user provides a username.
6) NAC forwards the username to the TACACS+ server.
7) NAC requests the password prompt from the TACACS+ server.
8) The TACACS+ server provides a password prompt.
9) NAC prompts the user for the password.
10) User submits the password.
11) NAC forwards the password to the TACACS+ server
12) The TACACS+ server accepts or rejects the user
The various messages used by TACACS+ are:
1) Accept
2) Reject
3) Error
4) Continue
Configuration of TACACS+
Router(config)# aaa new-model
Router(config)# tacacs-server host 10.0.0.1 single connection Router(config)# tacacs-server key shared2
802.1x
It is a port-authentication protocol used to stop unauthorized access in the network. When 802.1x is enabled in the network the switch will not pass the data to the user until the user
has been authenticated. It is the layer 2 protocol. The 802.1x can be implemented when both the client and the switch are 802.1x compatible. An 802.1x switch port begins in the unauthorized state so that no data other than the 802.1x protocol itself is allowed through the port. Either the client or the switch can initiate an 802.1x session. The authorized state of the port ends when the user logs out, causing the 802.1x client to inform the switch to revert back to the unauthorized state. The switches can also time out the user's authorized session. If this happens, the client must re-authenticate to continue using the switch port.
This port based authentication can be used with RADIUS servers. To configure 802.1x RADIUS must be configured first.
